Use shadowbroker SMBTOUCH tools to scan for vulnerable smb services so these machines can be identified and patched. Comes with x86 libraries. Target List option should be list of IPs separated by newline. This is based on SMBTOUCH from the shadowbroker dump.
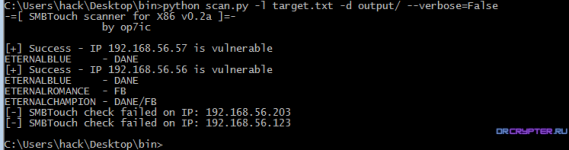
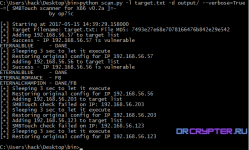
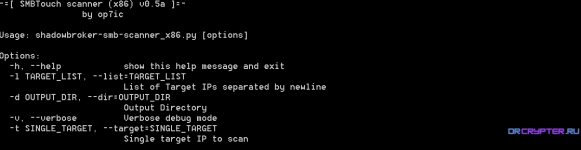



This is based on shadowborker dump. Who knows what hides in these binaries, use at your own risk and from VM ideally.
drcrypter.ru
Download LINK HERE :
Download LINK mirror #1 :
Download LINK mirror #2 :
Download LINK mirror #3 :
Download LINK mirror #4 :
Download LINK mirror #5 :
Download LINK mirror #1 :
Download LINK mirror #2 :
Download LINK mirror #3 :
Download LINK mirror #4 :
Download LINK mirror #5 :


