This tool is not just another SSH brute forcer; it's unique in allowing you to build your own username and password lists. You can generate as many usernames and passwords as you wish,
including combinations of digits and letters (both lowercase and uppercase). You can also choose to generate only digits, only letters, or both.
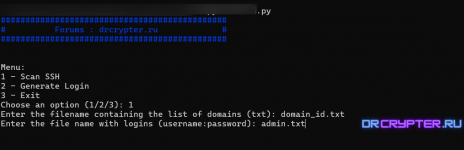
If this sounds complex, the pictures below will provide a clearer understanding.
Options in the Tool:
- Scan SSH
- Generate Login
What is SSH Brute Force and How Does It Work?
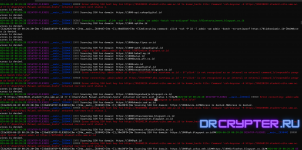
SSH (Secure Shell) brute force attacks involve systematically trying various username and password combinations to gain unauthorized access to a remote server running the SSH protocol.
The attack leverages automation to rapidly test large numbers of credential combinations until the correct one is found. Once access is obtained, the attacker can control the server, steal data, or use it for further malicious activities.
What is a Botnet SSH?
A botnet SSH refers to a network of compromised computers or devices (bots) that an attacker controls via SSH.
Once the attacker successfully logs into multiple devices using brute force or other methods,
they can issue commands to all the infected devices simultaneously. These botnets can be used for various malicious purposes, such as launching DDoS attacks, sending spam, or mining cryptocurrency.
module you need install ::
py3 or python3 -m pip install paramiko
py3 or python3 -m pip install termcolor
py3 or python3 -m pip install coloredlogs
py3 or python3 -m pip install signal
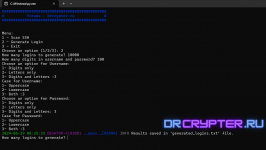
including combinations of digits and letters (both lowercase and uppercase). You can also choose to generate only digits, only letters, or both.
If this sounds complex, the pictures below will provide a clearer understanding.
Options in the Tool:
- Scan SSH
- Generate Login
What is SSH Brute Force and How Does It Work?
SSH (Secure Shell) brute force attacks involve systematically trying various username and password combinations to gain unauthorized access to a remote server running the SSH protocol.
The attack leverages automation to rapidly test large numbers of credential combinations until the correct one is found. Once access is obtained, the attacker can control the server, steal data, or use it for further malicious activities.
What is a Botnet SSH?
A botnet SSH refers to a network of compromised computers or devices (bots) that an attacker controls via SSH.
Once the attacker successfully logs into multiple devices using brute force or other methods,
they can issue commands to all the infected devices simultaneously. These botnets can be used for various malicious purposes, such as launching DDoS attacks, sending spam, or mining cryptocurrency.
module you need install ::
py3 or python3 -m pip install paramiko
py3 or python3 -m pip install termcolor
py3 or python3 -m pip install coloredlogs
py3 or python3 -m pip install signal





