Information Threads : MikroTik RouterOS through 6.42 allows unauthenticated remote attackers to read arbitrary files and remote authenticated attackers to write arbitrary files due to a directory traversal vulnerability in the WinBox interface.
What is affected?
The bug affects all MikroTik-branded routers and wireless equipment running RouterOS versions below 6.42.7 or 6.40.9 and requires network access to either the ports used by the WinBox management tool or the regular HTTP (S) management interface. It is additionally possible that the MikroTik API (used for automated device management) could be affected. Tenable also disclosed other, less severe vulnerabilities (mostly denial-of-service) affecting the same versions.
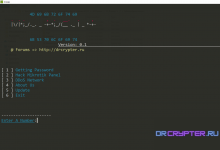
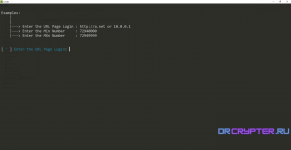
[ 1 ] Getting Password | Getting Password Cards Page Login My Network
[ 2 ] Hack Mikrotik Panel | Exploit Mikrotik Admin Panel
[ 3 ] DoDs Network | DoDs for Your NetWork
[ 4 ] About Us | My Information
[ 5 ] Exit | Logout in This Script
python3 -m pip install -r requirements.txt
python3 MikrotikSploit.py
What is affected?
The bug affects all MikroTik-branded routers and wireless equipment running RouterOS versions below 6.42.7 or 6.40.9 and requires network access to either the ports used by the WinBox management tool or the regular HTTP (S) management interface. It is additionally possible that the MikroTik API (used for automated device management) could be affected. Tenable also disclosed other, less severe vulnerabilities (mostly denial-of-service) affecting the same versions.
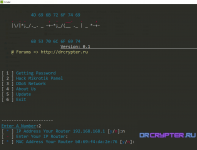
[ 1 ] Getting Password | Getting Password Cards Page Login My Network
[ 2 ] Hack Mikrotik Panel | Exploit Mikrotik Admin Panel
[ 3 ] DoDs Network | DoDs for Your NetWork
[ 4 ] About Us | My Information
[ 5 ] Exit | Logout in This Script
python3 -m pip install -r requirements.txt
python3 MikrotikSploit.py



drcrypter.ru
Last edited:


