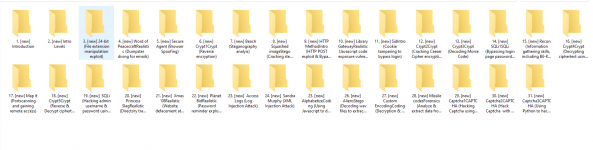
Learn Ethical Hacking CEH Course by Paul Chin Nulled :
I was split the lessons you can take part 2 with reverse engineering :
1. [new] Introduction
2. [new] Intro Levels
3. [new] 24-bit (File extension manipulation exploit)
4. [new] Word of PeacecraftRealistic (Dumpster diving for emails)
5. [new] Secure Agent (Browser Spoofing)
6. [new] Crypt1Crypt (Reverse encryption)
7. [new] Beach (Steganography analyis)
8. [new] Squashed imageStego (Cracking steganography)
9. [new] HTTP MethodIntro (HTTP POST exploit & Bypass CSRF-token protection)
10. [new] Library GatewayRealistic (Javascript code exposure vulnerability)
11. [new] SidIntro (Cookie tampering to bypass login)
12. [new] Crypt2Crypt (Cracking Caeser Cipher encryption)
13. [new] Crypt3Crypt (Decoding Morse Code)
14. [new] SQLi1SQLi (Bypassing login page password using SQL Injection Attack)
15. [new] Recon (Information gathering skills, including B6-Key)
16. [new] Crypt4Crypt (Decrypting ciphertext using online decryptors)
17. [new] Map It (Portscanning and gaining remote access)
18. [new] Crypt5Crypt (Reverse & Decrypt ciphertext using online decryptor)
19. [new] SQLi (Hacking admin username & password using SQL Injection Attack)
20. [new] Princess SlagRealistic (Directory traversal & null byte attacks)
21. [new] Xmas '08Realistic (Website defacement attacks)
22. [new] Planet BidRealistic (Password reminder exploits)
23. [new] Access Logs (Log Injection Attack)
24. [new] Sandra Murphy (XML Injection Attack)
25. [new] AlphabetizeCoding (Using Javascript to defeat countdown timer)
26. [new] AliensStego (Decoding wav files to extract passwords)
27. [new] Custom EncodingCoding (Decryption & hacking website countdown timer)
28. [new] Missile codesForensics (Analyze & extract data from disk images)
29. [new] Captcha1CAPTCHA (Hacking Captcha using OCR and AutoIt)
30. [new] Captcha2CAPTCHA (Hack Captcha with node.js, imagemagick & AutoIt )
31. [new] Captcha3CAPTCHA (Using Python to hack Captcha )
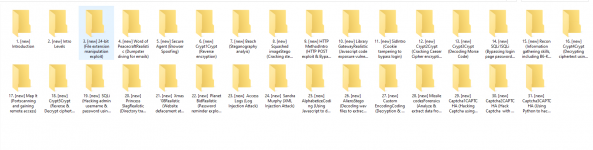
I was split the lessons you can take part 2 with reverse engineering :
1. [new] Introduction
2. [new] Intro Levels
3. [new] 24-bit (File extension manipulation exploit)
4. [new] Word of PeacecraftRealistic (Dumpster diving for emails)
5. [new] Secure Agent (Browser Spoofing)
6. [new] Crypt1Crypt (Reverse encryption)
7. [new] Beach (Steganography analyis)
8. [new] Squashed imageStego (Cracking steganography)
9. [new] HTTP MethodIntro (HTTP POST exploit & Bypass CSRF-token protection)
10. [new] Library GatewayRealistic (Javascript code exposure vulnerability)
11. [new] SidIntro (Cookie tampering to bypass login)
12. [new] Crypt2Crypt (Cracking Caeser Cipher encryption)
13. [new] Crypt3Crypt (Decoding Morse Code)
14. [new] SQLi1SQLi (Bypassing login page password using SQL Injection Attack)
15. [new] Recon (Information gathering skills, including B6-Key)
16. [new] Crypt4Crypt (Decrypting ciphertext using online decryptors)
17. [new] Map It (Portscanning and gaining remote access)
18. [new] Crypt5Crypt (Reverse & Decrypt ciphertext using online decryptor)
19. [new] SQLi (Hacking admin username & password using SQL Injection Attack)
20. [new] Princess SlagRealistic (Directory traversal & null byte attacks)
21. [new] Xmas '08Realistic (Website defacement attacks)
22. [new] Planet BidRealistic (Password reminder exploits)
23. [new] Access Logs (Log Injection Attack)
24. [new] Sandra Murphy (XML Injection Attack)
25. [new] AlphabetizeCoding (Using Javascript to defeat countdown timer)
26. [new] AliensStego (Decoding wav files to extract passwords)
27. [new] Custom EncodingCoding (Decryption & hacking website countdown timer)
28. [new] Missile codesForensics (Analyze & extract data from disk images)
29. [new] Captcha1CAPTCHA (Hacking Captcha using OCR and AutoIt)
30. [new] Captcha2CAPTCHA (Hack Captcha with node.js, imagemagick & AutoIt )
31. [new] Captcha3CAPTCHA (Using Python to hack Captcha )