What is a Botnet?
A botnet is a network of computers that are controlled by a bot herder infected with malware . The bot herder is the one who operates the botnet infrastructure and uses the compromised computers to launch attacks designed to crash a target’s network, inject malware, harvest credentials or execute CPU-intensive tasks. Each individual device within the botnet network is called a bot.

PASSWORD ZIP : drcrypter.ru
A botnet is a network of computers that are controlled by a bot herder infected with malware . The bot herder is the one who operates the botnet infrastructure and uses the compromised computers to launch attacks designed to crash a target’s network, inject malware, harvest credentials or execute CPU-intensive tasks. Each individual device within the botnet network is called a bot.
How are Botnets Controlled?
Bot herders control their botnets through one of two structures: a centralized model with direct communication between each computer and the bot herder, and a decentralized system with multiple links between all the infected botnet devices.
Centralized, Client-Server Model
The first generation of botnets operated on a client-server architecture, where one command-and-control (C&C) server operates the entire botnet. Due to its simplicity, the disadvantage of using a centralized model over a P2P model is that it is susceptible to a single point of failure.
The two most common C&C communication channels are IRC and HTTP:
IRC (Internet Relay Chat) botnet
IRC botnets are among the earliest types of botnet and are controlled remotely with a pre-configured IRC server and channel. The bots connect to the IRC server and await the bot herder’s commands.
HTTP botnet
An HTTP botnet is a web-based botnet through which the bot herder uses the HTTP protocol to send commands. Bots will periodically visit the server to get new commands and updates. Using HTTP protocol allows the herder to mask their activities as normal web traffic.
Bot herders control their botnets through one of two structures: a centralized model with direct communication between each computer and the bot herder, and a decentralized system with multiple links between all the infected botnet devices.
Centralized, Client-Server Model
The first generation of botnets operated on a client-server architecture, where one command-and-control (C&C) server operates the entire botnet. Due to its simplicity, the disadvantage of using a centralized model over a P2P model is that it is susceptible to a single point of failure.
The two most common C&C communication channels are IRC and HTTP:
IRC (Internet Relay Chat) botnet
IRC botnets are among the earliest types of botnet and are controlled remotely with a pre-configured IRC server and channel. The bots connect to the IRC server and await the bot herder’s commands.
HTTP botnet
An HTTP botnet is a web-based botnet through which the bot herder uses the HTTP protocol to send commands. Bots will periodically visit the server to get new commands and updates. Using HTTP protocol allows the herder to mask their activities as normal web traffic.
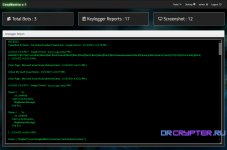
Keylogger
Clipper
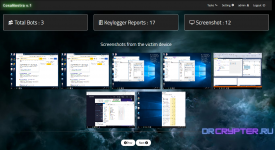
Screenshot
Stealer Files (Photos , Docs , TXT)
Download and Execute (Loader)
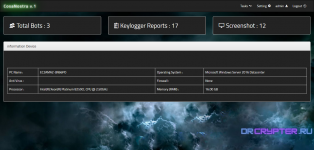
Get information Device [PC Name , Operating System , Firewall , Memory (RAM) , Anti Virus , Processor ]
Get location and address
Clear Cookies and Session from 20 Browsers like [ Google Chrome , Mozilla Firefox , Opera , Yandex etc...]
Anti-Sandbox like [ wireshark , Process Hacker , TCPVIEW , virtualBox , sandboxie etc... ]
Clipper
Screenshot
Stealer Files (Photos , Docs , TXT)
Download and Execute (Loader)
Get information Device [PC Name , Operating System , Firewall , Memory (RAM) , Anti Virus , Processor ]
Get location and address
Clear Cookies and Session from 20 Browsers like [ Google Chrome , Mozilla Firefox , Opera , Yandex etc...]
Anti-Sandbox like [ wireshark , Process Hacker , TCPVIEW , virtualBox , sandboxie etc... ]
# dynamic Pages
# Responsive pages [You can use it from a phone]
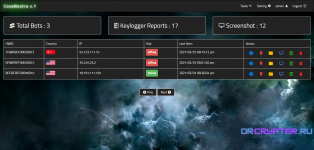
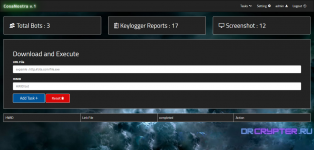
# Home page you can see all bots and counters like [Total Bots , Keylogger Reports , Screenshot ]
and info like [HWID , Country IP , Stat ( online or offline), Last Seen ]
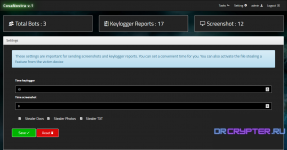
# Settings Page
from this page You can set a convenient time for you. You can also activate the file stealing a feature from the victim device
# Tasks Page you can add task Download and Execute or delete tasks
# User Page you can Change User information
# Responsive pages [You can use it from a phone]
# Home page you can see all bots and counters like [Total Bots , Keylogger Reports , Screenshot ]
and info like [HWID , Country IP , Stat ( online or offline), Last Seen ]
# Settings Page
from this page You can set a convenient time for you. You can also activate the file stealing a feature from the victim device
# Tasks Page you can add task Download and Execute or delete tasks
# User Page you can Change User information







PASSWORD ZIP : drcrypter.ru


