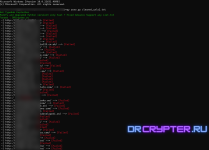
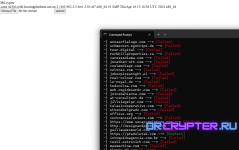
Bot TypeHub Exploiter
Modify and Upgraded Python version3 very Fast + Fixed Advance Support any List.txt
you must have installed python3 and install pip as command : python3 zero.py list.txt
If got result will save into Shells.txt
What is CVE and how it work ?
🚨 CVE-2021-25094 ( Tatsu < 3.3.12 Unauthenticated RCE) 🚨
If you using the Tatsu WordPress plugin below version or under 3.3.12
you might be sitting on a ticking time bomb 💣 LOL.
This critical vulnerability lets attackers run any code on your server without even logging in—yikes! 😱
🔍 What’s the Issue?
Tatsu had a flaw in its custom font upload feature that allowed hackers to:
⚡ Upload malicious files (like a backdoor PHP script) via an unauthenticated request.
⚡ Bypass security checks by hiding their files using tricky naming conventions (.shell.php).
⚡ Execute arbitrary commands remotely, potentially taking over your website.
🛑 What Can Happen?
If exploited, this can lead to:
🚨 Full site takeover – Hackers can gain complete control over your WordPress site.
📂 Data theft – Private user info, customer data, and admin credentials could be exposed.
💣 Malware injection – Attackers can use your server for phishing, crypto mining, or other shady activities.
💀 Blacklisting & SEO damage – Google may flag your site as malicious, tanking your rankings.
🛠️ How to Stay Safe?
✅ Update your Tatsu plugin to version 3.3.13 or later ASAP! 🚀
✅ Scan your uploads folder (wp-content/uploads/typehub/custom/) for suspicious files.
✅ Enable a Web Application Firewall (WAF) to block sketchy requests.
✅ Restrict file uploads to only trusted users.
✅ Monitor logs for unexpected admin actions or file changes.
Modify and Upgraded Python version3 very Fast + Fixed Advance Support any List.txt
you must have installed python3 and install pip as command : python3 zero.py list.txt
If got result will save into Shells.txt


What is CVE and how it work ?
🚨 CVE-2021-25094 ( Tatsu < 3.3.12 Unauthenticated RCE) 🚨
If you using the Tatsu WordPress plugin below version or under 3.3.12
you might be sitting on a ticking time bomb 💣 LOL.
This critical vulnerability lets attackers run any code on your server without even logging in—yikes! 😱
🔍 What’s the Issue?
Tatsu had a flaw in its custom font upload feature that allowed hackers to:
⚡ Upload malicious files (like a backdoor PHP script) via an unauthenticated request.
⚡ Bypass security checks by hiding their files using tricky naming conventions (.shell.php).
⚡ Execute arbitrary commands remotely, potentially taking over your website.
🛑 What Can Happen?
If exploited, this can lead to:
🚨 Full site takeover – Hackers can gain complete control over your WordPress site.
📂 Data theft – Private user info, customer data, and admin credentials could be exposed.
💣 Malware injection – Attackers can use your server for phishing, crypto mining, or other shady activities.
💀 Blacklisting & SEO damage – Google may flag your site as malicious, tanking your rankings.
🛠️ How to Stay Safe?
✅ Update your Tatsu plugin to version 3.3.13 or later ASAP! 🚀
✅ Scan your uploads folder (wp-content/uploads/typehub/custom/) for suspicious files.
✅ Enable a Web Application Firewall (WAF) to block sketchy requests.
✅ Restrict file uploads to only trusted users.
✅ Monitor logs for unexpected admin actions or file changes.


