BrakTooth Sniffer - is an active BR/EDR sniffer that can be used to study the Bluetooth (BT) BR/EDR interaction between the ESP32 controller and a remote target.
Scheme for intercepting Bluetooth using a sniffer on ESP32.
Unlike passive sniffer devices that do not communicate with a Bluetooth network (piconet), an active sniffer connects to a remote Bluetooth device (BR/EDR target) and allows you to test the Bluetooth protocol.
The BrakTooth sniffer supports cheap boards like ESP32-DOIT ($4) or ESP32-DevKitC ($10).
Scheme for intercepting Bluetooth using a sniffer on ESP32.

Unlike passive sniffer devices that do not communicate with a Bluetooth network (piconet), an active sniffer connects to a remote Bluetooth device (BR/EDR target) and allows you to test the Bluetooth protocol.
The BrakTooth sniffer supports cheap boards like ESP32-DOIT ($4) or ESP32-DevKitC ($10).
Installing BrakTooth Sniffer
Clone the repository:
Go to directory:
Install the latest version of Wireshark and Python3 (requires sudo):
Building the Bluetooth host programs and the Wireshark h4bcm dissector:
git clone https://github.com/Matheus-Garbelini/esp32_bluetooth_classic_snifferGo to directory:
cd esp32_bluetooth_classic_snifferInstall the latest version of Wireshark and Python3 (requires sudo):
./requirements.shBuilding the Bluetooth host programs and the Wireshark h4bcm dissector:
./build.sh
BrakTooth Sniffer ESP32 Firmware
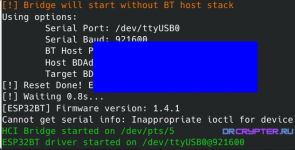
Before you can start using BrakTooth Sniffer, you need to upload custom firmware to your ESP32:
Change ttyUSB0 to your port.
./firmware.py flash /dev/ttyUSB0Change ttyUSB0 to your port.
Using BrakTooth Sniffer
Syntax:
Usage options:
--port TEXT - port name (/dev/ttyUSBx for Linux).
--host TEXT - BDAddress of the local host (default: E0 4:E8:19:C7:68).
4:E8:19:C7:68).
--target TEXT - BDAddress of the remote target (for example: a8:96:75:25:c2:ac).
--live-wireshark - open a live Wireshark session
--live-terminal - display a summary of each packet in the terminal.
--bridge-only Starts an HCI bridge without connecting to the Bluetooth host stack.
--help Show message and exit.
You can use the sniffer as master or slave. If you specify the --target option, the sniffer will connect to the remote target. If you do not use this argument, it will be in standby mode, waiting for a connection to it.
Argument--bridge-onlyonly creates an HCI pseudo-terminal ( /dev/pts/x), so the ESP32 can act as a standard HCI Bluetooth controller. You can use this feature to connect any other Bluetooth host stack to the ESP32.
Consider examples of using the BrakTooth sniffer.
BTSnifferBREDR.pyUsage options:
--port TEXT - port name (/dev/ttyUSBx for Linux).
--host TEXT - BDAddress of the local host (default: E0
--target TEXT - BDAddress of the remote target (for example: a8:96:75:25:c2:ac).
--live-wireshark - open a live Wireshark session
--live-terminal - display a summary of each packet in the terminal.
--bridge-only Starts an HCI bridge without connecting to the Bluetooth host stack.
--help Show message and exit.
You can use the sniffer as master or slave. If you specify the --target option, the sniffer will connect to the remote target. If you do not use this argument, it will be in standby mode, waiting for a connection to it.
Argument--bridge-onlyonly creates an HCI pseudo-terminal ( /dev/pts/x), so the ESP32 can act as a standard HCI Bluetooth controller. You can use this feature to connect any other Bluetooth host stack to the ESP32.
Consider examples of using the BrakTooth sniffer.
Connecting to a Remote Target (Master )
./BTSnifferBREDR.py --port=/dev/ttyUSB0 --target=E0:D4:E8:19:C7:69 --live-terminal --live-wireshark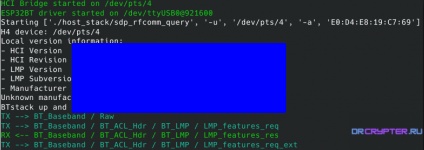
Bluetooth Connection Waiting (Slave )
./BTSnifferBREDR.py --port=/dev/ttyUSB0 --live-terminal --live-wireshark