An HTTP botnet is a web-based botnet through in which the bot herder uses the HTTP protocol to send commands.
Bots will occasionally visit the server to get updates and new commands.
Using HTTP protocol allows the herder to mask their activities as normal web traffic.
KratosKnife is a Advanced BOTNET Written in python 3 for Windows OS.
Provide With Lot of Advanced Features such as Persistence & VM Detection Methods, Built-in Binder, etc
*Dynamic Features
-Encrypt Source Code Using AES 256 Bit Encryption
-Encrypt Source Code Using Base64 Encoding
-Packing Evil Exe Using UPX Packer
-Interactive Mode [Generator Ask Required Parameter]
-Debug Mode [Can Be Used In Debugging Payload]
-Persistence Payload
-3 Powerfull Methods to Detect/Bypass VM (such as VirtualBox, VMware, Sandboxie)
-Built-in File Binder
-Useful Icons Inside icon Folder
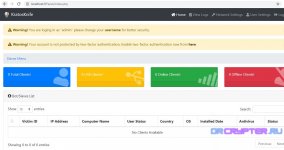
Commands Available In Attacker/Admin Panel
*Clients Command
1. Ping
2. Upload & Execute File
3. Show MessageBox
4. Take Screenshot
5. Installed Software
6. Execute Scripts
7. Elevate User Status
8. Clear TEMP Folder
*Stealer
1. Steal Firefox Cookie
2. Steal Chrome Cookie
3. Steal Bitcoin Wallet
4. Steal WiFI Saved Password
*Location
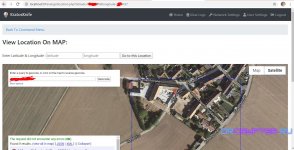
1. Get Location Information
2. Show Location On Map
*Open Webpage
1. Open Webpage (Visible)
*Computer Commands
1. Shutdown
2. Restart
3. Logoff
*Virtual Machine Bypass Methods Includes
-Registry Check
-Processes and Files Check
-MAC Adderess Check
Bots will occasionally visit the server to get updates and new commands.
Using HTTP protocol allows the herder to mask their activities as normal web traffic.
KratosKnife is a Advanced BOTNET Written in python 3 for Windows OS.
Provide With Lot of Advanced Features such as Persistence & VM Detection Methods, Built-in Binder, etc



*Dynamic Features
-Encrypt Source Code Using AES 256 Bit Encryption
-Encrypt Source Code Using Base64 Encoding
-Packing Evil Exe Using UPX Packer
-Interactive Mode [Generator Ask Required Parameter]
-Debug Mode [Can Be Used In Debugging Payload]
-Persistence Payload
-3 Powerfull Methods to Detect/Bypass VM (such as VirtualBox, VMware, Sandboxie)
-Built-in File Binder
-Useful Icons Inside icon Folder
Commands Available In Attacker/Admin Panel
*Clients Command
1. Ping
2. Upload & Execute File
3. Show MessageBox
4. Take Screenshot
5. Installed Software
6. Execute Scripts
7. Elevate User Status
8. Clear TEMP Folder
*Stealer
1. Steal Firefox Cookie
2. Steal Chrome Cookie
3. Steal Bitcoin Wallet
4. Steal WiFI Saved Password
*Location
1. Get Location Information
2. Show Location On Map
*Open Webpage
1. Open Webpage (Visible)
*Computer Commands
1. Shutdown
2. Restart
3. Logoff
*Virtual Machine Bypass Methods Includes
-Registry Check
-Processes and Files Check
-MAC Adderess Check
drcrypter.ru


