Cobalt Strike, based on Java after Armitage, looks like an outdate, right? Blackhats and hackers must be active world-wide by using Cobalt Strike's Beacon payload to target in real-time and attack any company in the world, as well as execute ransomware after gaining access to the company. Beacon is Cobalt Strike's payload for modeling advanced attackers. Use Beacon to egress a network over HTTP, HTTPS, or DNS. You may also limit which hosts egress a network by controlling peer-to-peer Beacons over Windows named pipes and TCP sockets.
How it work
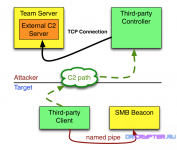
If you are a malware developer, you can learn more about evasion with these powerful tools that make it very easy to customize payloads or build your own to bypass real-time antivirus.
that is not only used for hackers or BlackHat, but RedTeam Expert used it to Penetration test companies with his own network as well, and the webserver has many features included automatically.
Beacon is flexible and supports asynchronous and interactive communication. Asynchronous communication is low-speed and slow. Beacon will phone home, download its tasks, and go to sleep. Interactive communication happens in real-time.
Setup SERVER - Follow the picture tutorial HERE :
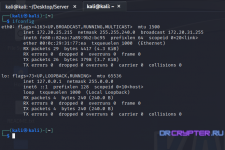
As a Server you need configure follow command step by step
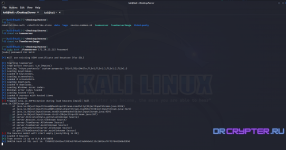
Message Error: That's not a problem; you just reboot the machine after you will see something like this.
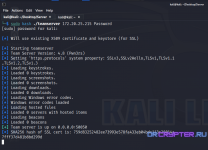
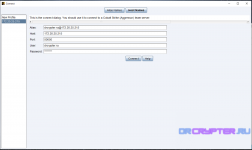
To start the client, go to Client, double-click cobaltstrike-client.cmd, and input your TeamServer data.
Explain: Alias is Username@Linux_IP or your Linux Server.
HOST Kali_Linux or your Linux Server
Port 50050
User drcrypter.ru
Password: Password (we have configuration ready in Kali Linux)
Information File : 212.2 Mb Cobalt Strike 4.8 Cracked + JDK-17 [ drcrypter ].zip
How it work

If you are a malware developer, you can learn more about evasion with these powerful tools that make it very easy to customize payloads or build your own to bypass real-time antivirus.
that is not only used for hackers or BlackHat, but RedTeam Expert used it to Penetration test companies with his own network as well, and the webserver has many features included automatically.
Beacon is flexible and supports asynchronous and interactive communication. Asynchronous communication is low-speed and slow. Beacon will phone home, download its tasks, and go to sleep. Interactive communication happens in real-time.
Setup SERVER - Follow the picture tutorial HERE :

As a Server you need configure follow command step by step

Message Error: That's not a problem; you just reboot the machine after you will see something like this.

To start the client, go to Client, double-click cobaltstrike-client.cmd, and input your TeamServer data.
Explain: Alias is Username@Linux_IP or your Linux Server.
HOST Kali_Linux or your Linux Server
Port 50050
User drcrypter.ru
Password: Password (we have configuration ready in Kali Linux)

drcrypter.ru
Information File : 212.2 Mb Cobalt Strike 4.8 Cracked + JDK-17 [ drcrypter ].zip


